Platform Architecture Overview
Our HypurrQuant Bot runs on a multi‑AZ, private‑subnet infrastructure to guarantee maximum security, isolation, and end‑to‑end encryption.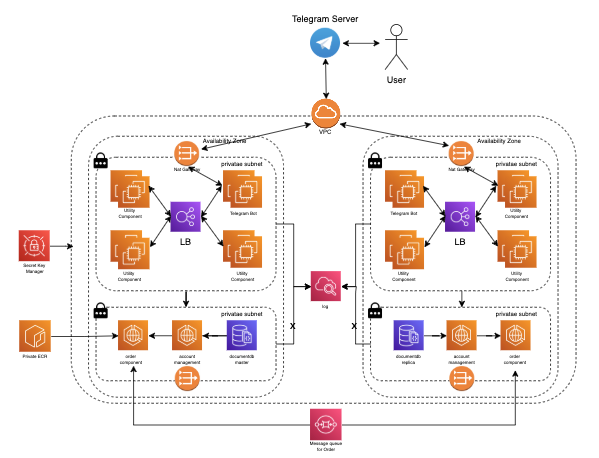
Detail of Our Encryption Architecture
1️⃣ Bot Server Obfuscation
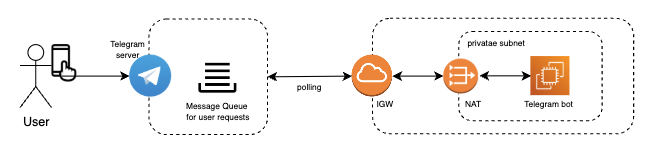
• Hidden endpoint: The bot server never exposes ports or IPs.
2️⃣ Fully Isolated Service Deployment
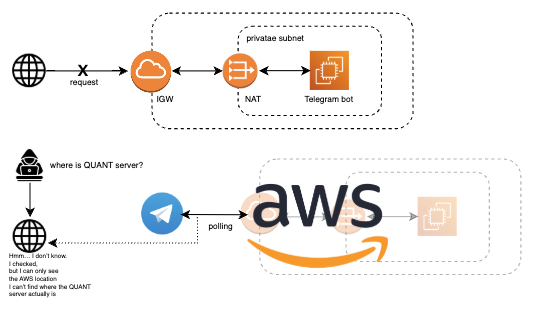
• Opaque networking: Intercepted packets reveal only AWS IGW, not our servers.
🚫 Attackers cannot see IPs, DNS, or ports.
3️⃣ Strict Data Access Control & No Logging Policy
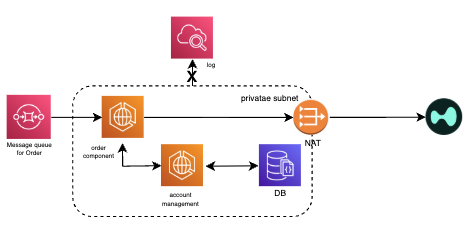
• No sensitive logs: No user data is ever written to disk or log streams.
4️⃣ Asymmetric Encryption-Based Order Processing
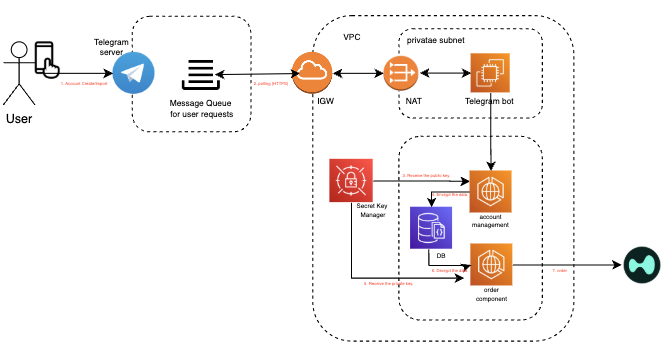
• Order Server isolation: Runs in a locked-down subnet, no open ports.
• Message‑driven: Receives SQS instructions, verifies, then decrypts in‑memory only and immediately purges.

